Web3 is here. By now, practically everyone has heard something about Web3; the decentralized web; the read/write/own web and all of that. We are still in the early stages of Web3, and it is okay to be completely confused about what exactly Web3 is. Maybe you know that it involves the blockchain, cryptocurrency, NFTs, DeFis, as well as other elements that have made their marks in the past few years. All of this might be too much to process, and honestly, I get it. Not up to half of the world's population are onboarded to Web3, so you're safe... for now😉.
However, Web3 is rapidly increasing in popularity. Just last month, I joined a writing competition organized by StackUp, in collaboration with Google, and during my research, I discovered that Google now offers to run self-managed blockchain nodes. Woah! If a Web2 giant like Google is building infrastructure to support Web3, then surely, it looks like Web3 is going to go off in our time. You don't want to be featured in a magazine years from now where it lists you, like that guy who spent all his Bitcoin on pizza, or the one who lost his cold wallet containing an insane amount of Bitcoin. No right? So now that we are still in the early stages, it is the right time to learn and contribute to building web3 and make your mark! Who knows, you might just build the next big thing!
In this article, we are going to be talking about one of the core elements that powers Web3; the Blockchain. This article will provide you with the basic knowledge you need to understand blockchain technology. It will cover the following:
what a blockchain is and how it works,
its features,
different types of blockchains,
use cases for the blockchain and what can be built on it,
its advantages and challenges,
how blockchain evolved beyond cryptocurrency,
and a short guide on how to get started interacting with a blockchain.
Prerequisites
This article is targeted towards beginners and assumes that the reader has no prior knowledge of blockchain technology.
What is a Blockchain?
The very first time I heard the word "Blockchain" years ago, I thought, surely this must mean a chain of blocks. I was absolutely right! it was a chain of blocks indeed. Although not in the exact way I thought. These blocks were digital, and they were chained using a cryptographic mechanism known as hashing.
What is a Block?
A block, in the concept of blockchain, refers to a container used to store a group of transaction records; usually transactions made around the same time. A typical block consists of a header and a body. The block header contains information like the previous block hash (we'll talk about what a hash is later), the current block hash, which is the block identifier, the time the block was created; known as the block timestamp, a summary of the transactions in the block; known as the Merkle root, and a random number known as the nonce. As well as additional details unique to each blockchain. While the body contains a list of validated transactions.
How are these blocks chained together?
Every block on a blockchain, from the genesis block (the very first block on the blockchain network) to the current block contains an identifier unique to only that block. This identifier is called a hash.
A hash is a fixed string of random characters generated from input data of any size through a mathematical algorithm. A hash will always return the same string of random characters for a particular output. However if the data input changes even slightly, it will return a totally different output. For example, using the Secure Hash Algorithm 256-bit (SHA-256) hashing technique, the hash of the string "WAGMI" is "4B5AECC6AE134D5A5564084034DBDEC35A90BC23423AF89E098432CEF86D93E6", while the hash of "WAGMi" is "D14A78DC1A47FDEB2394AA4D1058ABFB1544F2DDEDF481A9B8189FDDDF8048DA". Notice that a change as little as in the above example resulted in a totally different hash. Hashes are irreversible. There is no way to generate the input used to create the hash, from the hash. You can try generating hashes for files and strings here
When a block is created, it includes the hash of the previous block, along with its own hash. This is what links the current block to the previous block, and so on, all the way down to the Genesis block. This is also a security feature of the blockchain because changing data on one block will cause the block's hash to change. Since each block's hash is contained in the next block, this will be easily spotted and the network can penalize the participant who attempted this.
What then is a Blockchain?
Imagine you and your friends are saving money together and every time someone makes a deposit or a withdrawal, you all have this magic book where you write it down. This book can be replicated and works in such a way that when a new transaction is recorded in it or any of its replicas, it appears in every copy of the book. So that, at each point in time, anyone can make transactions and access data in the book if they want to without needing the original creator of the book. In this analogy, the pages in each book represent a block, the spine of the book which holds the pages together refers to the chain, and the book itself is the blockchain.
With all the information presented, you now know that a blockchain is a record of blocks containing transactions, which are linked to each other using hashes. Additionally, the blockchain is spread across a network of computers, each maintaining a copy of the blockchain. These computers are called nodes. Data on the blockchain cannot be easily changed because once it is uploaded to the blockchain, it is very difficult to alter. Changing data in a block requires changing data in other blocks since they are all linked. Moreover, since everyone has a copy of the blockchain on their computer, it will be quite easy to spot.
So to put together all these tidbits of information, we can say that a blockchain is simply a digitally distributed and immutable ledger that runs on a peer-to-peer network of nodes in a secure and transparent manner.
The term "Blockchain" is often used interchangeably with "Web3". The key difference is that while Web3 refers to the next phase of the internet that is focused on decentralization, blockchain is just one of the technologies that power Web3 to be decentralized. It is the most popular of Web3 technologies as it is the foundation on which features such as Cryptocurrencies and Decentralized Finance (De-Fi) are built. Blockchain is a technology, while Web3 is a vision that leverages this technology.
Key Features of the Blockchain
Blockchain solves the problem of trust, decentralization, and control of digital assets and digital identities which are associated with the current Web2 technologies. Blockchain operates with smart contracts which eliminate the need for intermediaries to carry out transactions.
Decentralization: Since copies of the blockchain are spread over a peer-to-peer network across the world, it simply means that the blockchain operates on a decentralized network where control does not lie on a single or central entity.
Transparency: Transactions are carried out in a transparent manner since anyone can easily view the details of any transaction that has been uploaded.
Immutability: Once information is uploaded to the blockchain, it is very difficult to change, as it will involve changing a lot of other data linked to it. Additionally, anyone can easily spot the changes on their own copy of the blockchain. This is a strong security feature of the blockchain as it helps to protect the network against malicious actors.
Consensus Mechanisms: Consensus mechanisms simply refer to the process through which participants in a blockchain network come to agree on the state of the network. The state of the network refers to the status of the network at any particular point in time. This includes the balances of accounts on the blockchain and the status of smart contracts deployed on the blockchain at that point in time. Common consensus mechanisms are Proof of Work used by Bitcoin and Proof of Stake used by Ethereum.
Smart Contracts: These are digital contracts that self-execute when the terms and conditions specified in them are met. These are what ensure transactions between network participants are carried out successfully, and without including a third party.
Cryptographic Key Pairs: Cryptographic key pairs are a pair of unique mathematically linked keys consisting of a public key and a private key. They are used in generating wallet addresses, signing transactions, encryption and decryption, and for user authentication. A message sent from one user to another user's public key can be decoded only by the user with the corresponding private key. Alternatively, when a user signs a message with their private key and sends the message, only the corresponding public key can be used to decode the message. This is a way to verify that the message is indeed coming from that particular user, as they are the only one that should have access to their private key.
Types of Blockchain
There are three types of Blockchain:
Public Blockchain
Private (Permissioned) Blockchain
Consortium Blockchain
Public Blockchains: This is unarguably the most common type of blockchain. Here, the blockchain is open to the public, and anyone can access it, as well as read data from it and write data to it. This blockchain is also governed by its participants. Examples of public blockchains include Bitcoin, Ethereum and Solana.
Private Blockchains: This kind of blockchain can be likened to an organization where only its members can access the blockchain.
In some private blockchains, the blockchain itself can be viewed by the general public, maybe for the purpose of informing them on what's going on within the organization, or for educational purposes. However, carrying out transactions, the consensus process, governance, and dispute resolution are limited to only participants.
Membership in a private blockchain is controlled by the entity or organization that controls the blockchain. Private blockchains are commonly used in settings where an organization wants to leverage blockchain technology for specific applications without exposing sensitive information to the public. Additionally, they often have faster transaction processing times compared to public blockchains, since there are fewer nodes participating in consensus. It is like a workspace where everyone connects their computers to each other and all activities carried out can be seen by anyone whose computer is in that peer-to-peer network
Consortium Blockchains: If the private blockchain can be likened to an organization, a Consortium blockchain can be seen as an enterprise or a group of organizations. These are usually small-scale blockchains that are limited to organizations and not open to the public. Here, the only participants who can access or read/write data to the blockchain are members of these organizations. Governance may be open to all members of the organization, or limited to high-ranking members. Consortium blockchains are commonly used in settings like Healthcare data management where an enterprise or a group of partnered organizations want to exchange and track data in a secure and transparent manner.
Real-World use cases for Blockchain
The most popular use for Blockchain is De-Fi. This might be because the first use of the blockchain was to transact cryptocurrency. However, over the years blockchain technology has emerged as a trusted solution to a lot of other real-world problems. Below are some everyday use cases where blockchain technology is employed:
Supply Chain Management
Digital Identity and Authentication
Intellectual property and Royalty distribution
Tokenization of assets
Voting systems
Healthcare Data Management
Gaming
The major use cases for blockchain revolve around situations where there is a need for peer-to-peer contact, and/or data needs to be made public to ensure its authenticity and allow ease of access.
What can be built on the Blockchain?
Anything really! A common misconception is that only a particular type of project or apps written in a particular language can be deployed to the blockchain. This is not true. Any Web2 project can be deployed to the blockchain. What you should consider when building on the blockchain is the purpose of the project. The problem you're trying to solve with your project. Is it a problem that the blockchain offers a solution to? If yes, then sure! go right ahead! For example, there are a lot of De-Fis on the blockchain, this is because the finance sector is one that needs to be decentralized. The need for the removal of third parties and intermediaries in financial processes is one the blockchain solves with its trustless and transparent feature. However, if you wanted to build something like a generic weather app, there's really no need to deploy it to the blockchain, as it does not have any problems the blockchain could solve.
If you've decided that your project offers a solution that aligns with blockchain technology, then the next thing you should consider is the blockchain to build on. Just as you would select a programming language based on your project's requirements, the same with blockchains. Does it need low gas fees, fast transactions, etc? There is a wide variety to choose from, you just have to do your research and decide which blockchain aligns best with your project.
Advantages of building on the blockchain
Due to the distributed nature of the blockchain, there is no single point of failure for apps and smart contracts running on the blockchain.
Since all transactions on the blockchain are visible to the public, users don't even need to trust you before they interact with your app, since they can easily verify any transaction themselves.
The removal of intermediaries significantly reduces transaction costs and processing speed for blockchain-based projects.
With blockchain technology still in its early stages, there is a lot of opportunity for builders in this space to explore and create innovative solutions.
The immutable nature of the blockchain greatly reduces fraud and solves the "double-spending" problem.
Challenges Faced by Blockchains
Energy Consumption: Blockchains like Bitcoin that use the Proof of Work consensus mechanism require a large amount of energy due to the machines involved in the mining process.
Immutability: While this is an advantage, it is also a limitation as well. This feature makes it difficult to update vulnerable smart contracts deployed to a blockchain. Instead, a new smart contract is written and all other smart contracts that read data from the previous smart contract have to be updated as well.
Legal Regulation: Cryptocurrency is yet to be accepted widely. There are concerns that it could easily be used for fraudulent practices, and as such it is subject to ever-changing regulations.
Storage requirements: While the blockchain network is growing, more data needs to be processed, which means the storage requirements to run a node will continue to increase. This could potentially mean that at some point, running a full node on the network might be accessible to fewer participants.
Scalability: As the network grows, there will be more transactions to be processed, which will slow down the processing speed and cause delays or network congestion.
Understanding The Blockchain Trilemma
The blockchain trilemma is a term used to describe the three properties desired in a single blockchain in order to improve its performance. The properties are:
Scalability
Security
Decentralization
The term "trilemma" is used because oftentimes, if one aspect is improved, it comes at the expense of another one. For example, if a blockchain attempts to improve its scalability, it might come at the expense of its decentralization because for the blockchain to achieve consensus, it might have to employ a mechanism that reduces or limits the number of nodes on the network to increase transaction processing speed. This will mean that the network is not open for a random user to participate in, and if so, is the network truly decentralized then?
Solutions to the Blockchain Trilemma
Over the years there have been a few solutions to the blockchain trilemma. Below are the commonly adopted ones:
Sharding: A blockchain network might decide to divide itself into smaller segments known as shards so it can handle and validate more transactions at the same time. Each shard is a mini-blockchain that operates independently, maintains its own transaction ledger and executes smart contracts. Instead of having all the nodes in the network process each transaction, a transaction from an account will be processed by the shard in the network that contains that account. Sharding in a network allows for parallel processing since different transactions can be processed by different shards in the network at the same time. Periodically, a summary of each shard's state will be included in the main blockchain, this is known as a "crosslink" This reduces the time taken to process a transaction on the network. An example of a blockchain employing the sharding technique is ZIlliqa.
Side Chains: As the name implies, this is a blockchain that runs alongside the Layer 1 and is interoperable with it. Sidechains are independent, and they possess features that may not be available on the main chain, allowing users to perform certain operations unique to only the sidechain. Additionally, since they are interoperable with the main chain, they also allow the user to transfer assets and data between the main chain and the sidechain. Sidechains allow the mainchain to extend its functionality and reduce load by allocating some operations to the sidechain. This improves transaction scalability and innovation whilst still maintaining security. An example of a sidechain is Plasma.
Layer 2s: Some blockchains are built on top of other blockchains, and they inherit the foundational standards and protocols. Foundational blockchains are called Layer 1s. Some popular Layer 1s are Bitcoin and Ethereum. On these Layer 1s, we can build other blockchains such as referred to as Layer 2s
A Layer 2 is a protocol built on a Layer 1 to offer a solution to one of the 3 problems Layer 1s face. For example, a Layer 2 can be built to reduce transaction costs as in the case of Arbitrum which is a Layer 2 on Ethereum, or to increase transaction throughput. These Layer 2s are built following the base protocols set by the Layer 1, and then with their own additional features. Transactions carried out on Layer 2s are also recorded on the Layer 1 in batches. From time to time, the Layer 2 will record a summary of the grouped transactions on the Layer 1. This is referred to as a "commitment" or "checkpoint".
Below are some of the common types of Layer 2s:
State Channels: These can be seen as mini blockchains where the participants carry out and record transactions among themselves in an off-chain environment. Then instead of updating the main blockchain with each transaction, only major updates involving the state of this blockchain are sent to the main blockchain. These updates could be operations like opening or closing of the channel, or in a case of dispute. This improves the speed, and scalability, while the participants enjoy the security provided by the main blockchain.
Rollups: Rollups are scaling solutions that carry out and record transactions off-chain, then bundle up a set of transactions in a batch as a single data, and send this data to the Layer 1. There are two types of rollups:
Optimistic Rollups: They operate on the assumption that the majority of the transactions are valid, this is the "optimistic" part of the rollup. After the batch data is sent, there is a "challenge" period during which any network participant can review the submitted data and raise concerns if any fraudulent activity is noted. The participant does this by generating and submitting something called a "fraud-proof". This fraud-proof is evidence that a specific transaction in a batch is invalid. The fraud-proof contains information about the invalid transaction along with cryptographic evidence that the transaction is indeed invalid. If the main chain verifies the fraud-proof and discovers invalid transactions within the batch, the invalid transactions will be reversed and the participants responsible for those transactions may be penalized.
ZK-Rollups: These use a cryptographic technique known as "Zero-knowledge proof" to compress the transactions data in a batch into a single proof known as the zero-knowledge proof. Unlike optimistic rollups, instead of sending the batch data along with the proof, only the zero-knowledge proof is sent. As the name implies, zero-knowledge proof operates in a way that shows that all the transactions contained in that batch are valid, without actually revealing the details of the transactions themselves. This improves security and scalability on the network.
How Blockchain Evolved Beyond Cryptocurrency
The first blockchain network; Bitcoin, was built in 2008 to provide a secure means to enable peer-to-peer transactions of digital currency without an intermediary.
Ethereum, proposed by Vitalik Buterin, discovered a bigger and much larger use for blockchains. The main idea was that since the blockchain was a peer-to-peer network of nodes, these nodes could serve as what we know in web2 as servers, and this network of nodes would be decentralized since each node is owned by different people and not a single organization. Ethereum sped up the phase of the internet we now know as Web3. With Ethereum came flexibility in blockchain technology. It brought about the De-Fis, Decentralized Autonomous Organizations, Decentralized Apps, etc because it came with Solidity, the Ethereum Virtual machine (EVM) smart contract language which was not as rigid as Bitcoin's Clarity.
Bitcoin vs Ethereum
| Bitcoin | Ethereum |
| Its main purpose was to facilitate the transaction of digital assets (cryptocurrency) without any need for an intermediary. | Its main purpose was to extend the use of blockchain beyond transferring assets. |
| Uses Proof of Work as a consensus mechanism | Uses Proof of Stake as a consensus mechanism |
| Clarity, which is the smart contract language for Bitcoin is rigid and only supports basic applications and protocols | Solidity, the smart contract language for the Ethereum Virtual Machine (EVM) supports practically anything to be built on Ethereum |
| Larger block size and slower transaction processing speed | Smaller block size and Faster processing speed |
Getting Started with Blockchain
The first thing you need to have in order to interact with the blockchain is a crypto wallet. A crypto wallet is a tool that allows you to keep track and control of your digital assets on the blockchain. It does this by creating the public and private key pair that serves as your identity on the blockchain and gives you control over your assets. The crypto wallet doesn't store these assets, it just keeps track of them for you and provides you with the ability to carry out transactions with your assets.
These assets are tied to your private key, which is particularly what gives you control of them. This is why if you lose your wallet, you do not lose your assets, but if you lose your private key, you cannot access your assets. You might be able to view them on a block explorer by searching your account address, but the ability to access them lies with the private key. Do not lose your private key!
When you create an account using a crypto wallet, What the wallet does is use a cryptography mechanism to create a private key. A private key is simply a 256-bit string that is secure due to the randomness of the characters in the string. From your private key, a public key is generated. This is why they are called "key pairs". Each public key has only one private key it is bound to. From your public key, your account address is then generated. This is the address you use for receiving assets, and this is the address that your identity on the blockchain is associated with. Simply put, this address is what represents you on the blockchain.
If you've used a crypto wallet, you'll notice that you can create a series of accounts within one wallet, and you'll notice a bunch of 12 or 24 random words called a "seed phrase" A seed phrase is like the master password for your wallet. While each account on your wallet is tied to its private key, all the accounts are tied to the seed phrase. Also, do not lose your seed phrase!
Types of Crypto Wallets
There are different types of crypto wallets. Up till now, you might've been picturing Metamask, Binance or Trust Wallet while we mentioned crypto wallets. While Binance is a Centralized Exchange and not necessarily a crypto wallet, the other two are the same type of crypto wallets; Online or Hot wallets. Below are the different types of crypto wallets briefly explained:
Hot Wallets: These are wallets that exist online, that you can download and make use of only while connected to the internet. They include Web wallets, mobile wallets like Coinbase, and desktop wallets.
Cold Wallets: These are physical, offline crypto wallets. They are a safer option than hot wallets because they are less vulnerable to online attacks. They include hardware wallets like LedgerNano or paper wallets; which are basically your private and public key on paper with a barcode that can be scanned.
We are going to guide you through the process of setting up Metamask. Metamask is a popular, secure and flexible crypto wallet. It has both a mobile version and a Chrome extension. It is also Open Source and benefits from a large community of developers. The steps below will show you how to install Metamask, create an account, buy Ethereum tokens, receive and send testnet tokens, and interact with dApps on the blockchain.
Installing Metamask
Head over to https://metamask.io/download/ and download Metamask for your browser.
After Metamask is installed, you will be prompted to create a password to login to Metamask.
Create a New account by selecting "Create an Account" and following the process to verify. Remember to store your seed phrase securely offline or with a key manager. Do not store it as screenshots on your phone, or in an email.
How to Buy, Send, and Receive Cryptocurrencies using Metamask
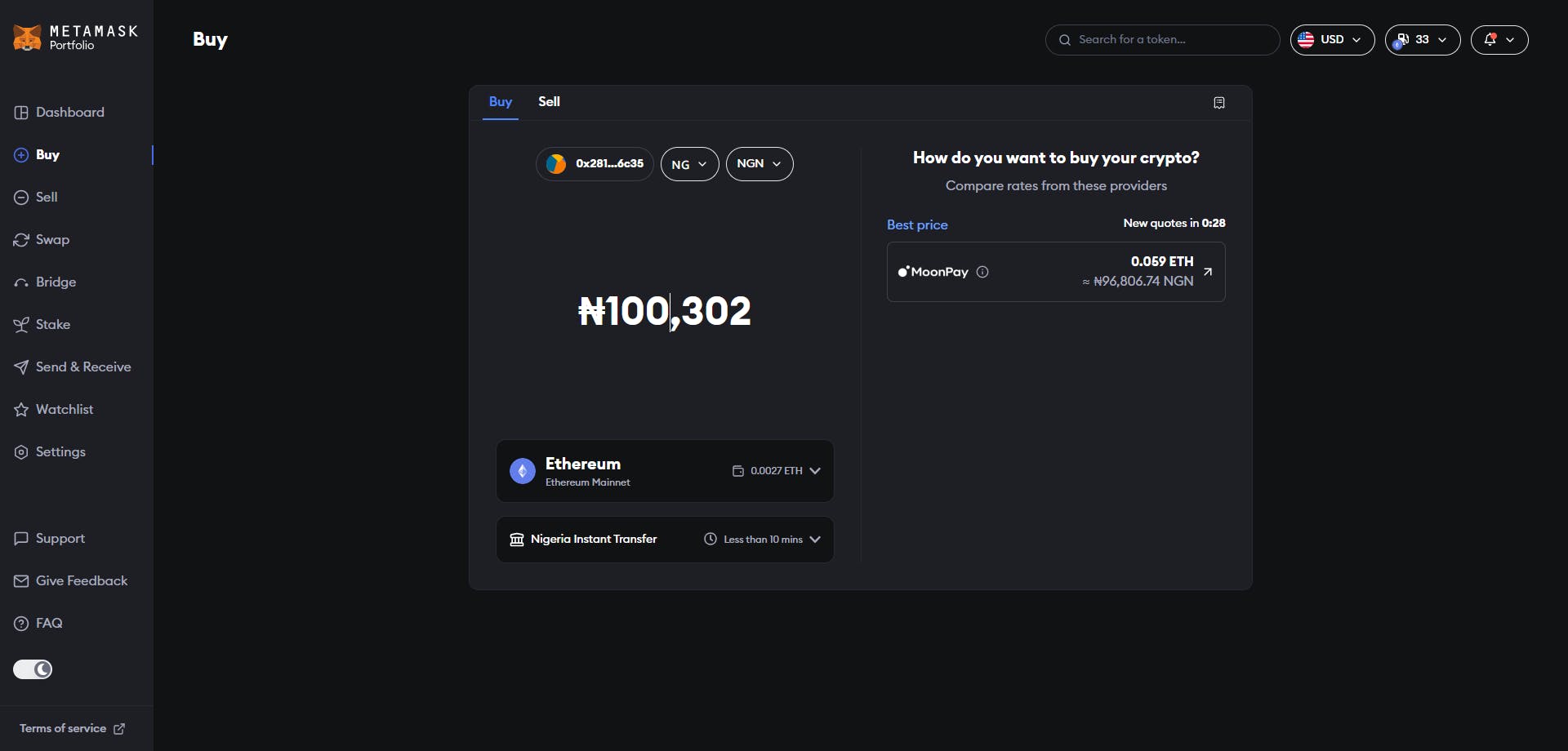
To Buy tokens on Metamask, Metamask connects you to a decentralized exchange (DEX) where you can purchase your desired tokens with your local currency.
Click on the "buy" icon on the homepage. It should take you to their Metamask portfolio page where you will select your country and payment method.
Next, input the amount of ETH you want to buy in your local currency. It should generate a list of providers, with the best value at the top of the list.
On Selecting a provider, you will be redirected to the DEX to sign in, complete a short verification process, and make payment.
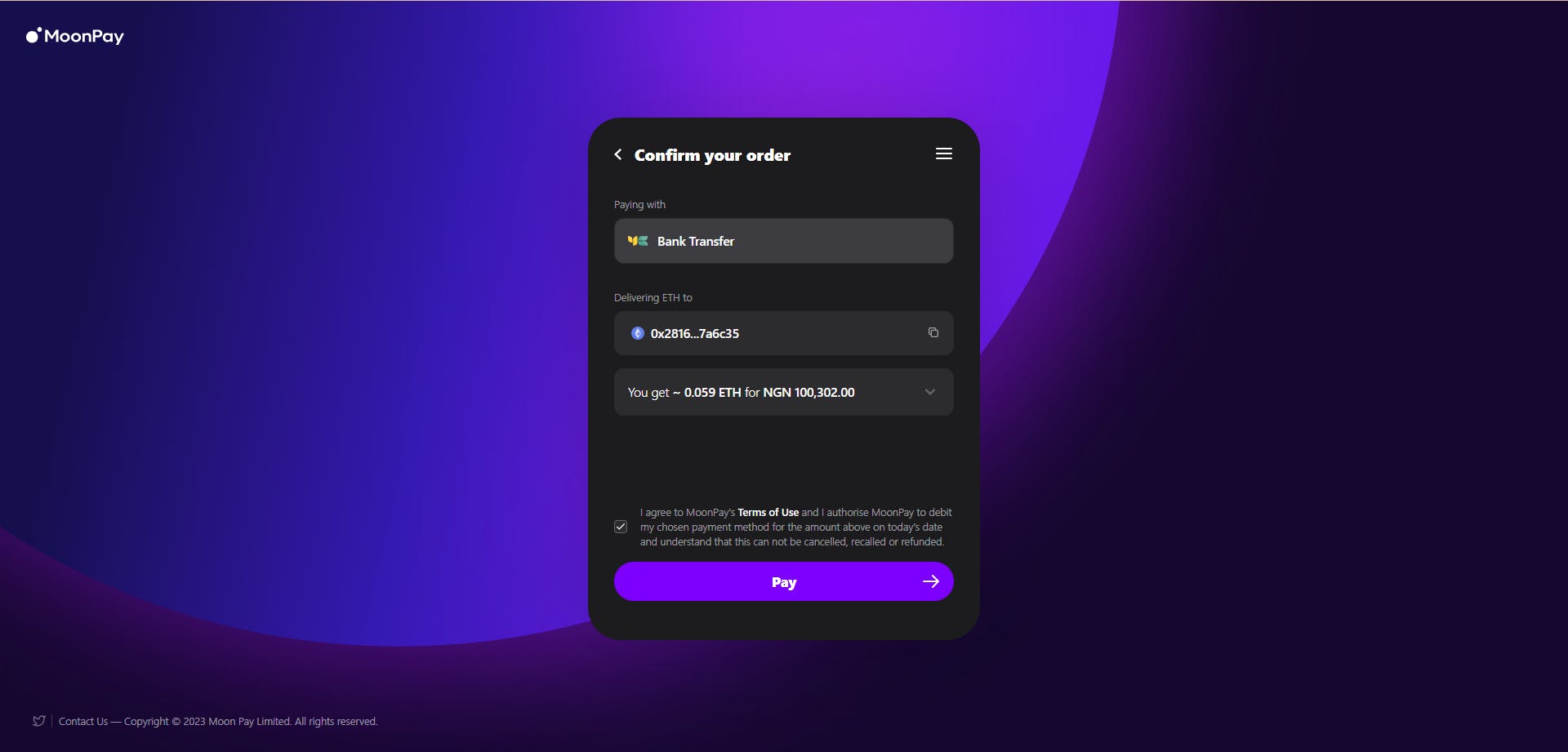
Once you have made the payment, the tokens will be reflected in your account balance within a few minutes.
Sending and Receiving Cryptocurrency
For this, we are going to use a testnet and testnet tokens. A tenet is a simulation of the real blockchain. It is a development environment that works in the same way the mainnet would work, and it is built for testing transactions, smart contracts and dApps before deploying them to the mainnet. We will test sending and receiving Sepolia ETH on the Sepolia testnet. Sepolia ETH has no real value and you can get some for free from a faucet.
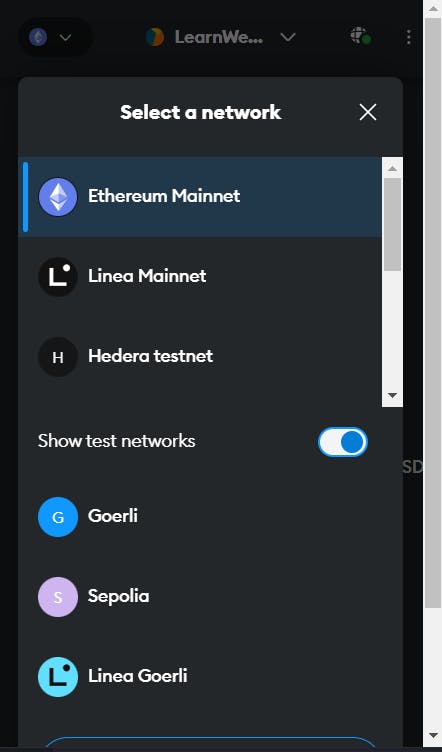
Switch to the Sepolia testnet. Click on the icon at the top left and select "Sepolia" under test networks.
Click on your account address to copy it, then head over to the Alchemy Sepolia faucet, paste the address and request ETH. Within a few minutes, the tokens should be reflected in your balance.
Create another account by clicking on the account dropdown at the top and selecting "add account". Give the account any name of your choice.
Copy the address of the account you just created and navigate back to the first account from the account dropdown.
Click on "Send" and paste the address in the address bar. Confirm that it is the same address by cross-checking the first and last 6 digits of the address. Alternatively, since it's just another account in the same wallet, you can simply select it from the list of addresses under "Your accounts".

Input the amount of Sepolia ETH you want to send, click next, and then confirm the transaction. Within a few seconds, the transaction should be confirmed on the network. You can check the balance of the recipient account to confirm it has been reflected.

Click on the transaction to view the details. Then click "View on block explorer to view your transaction on the block explorer.
Exploring a Blockchain Explorer
A blockchain explorer is simply a website where one can view the contents of the blockchain at any point. This includes blocks, transactions, addresses, and other data. The state of the blockchain refers to the transactions and other interactions on the blockchain from the genesis block to the current block.
Now that you are still on the block explorer, try searching for one of your account addresses in the search bar. You can also go to the Home page to view the latest blocks and transactions to see what a block on the blockchain actually looks like!
Interacting with dApps using Metamask
DApps usually have the option of connecting your wallet, this is the equivalent of creating an account in Web2. DApps usually provide detection for popular wallets like Metamask, Trust Wallet, Coinbase, etc. If you are using a less popular wallet, you might have to manually connect it. We are still going to be using a test account for security reasons. Do not use an account with real tokens to practice this! You might connect to a malicious site and your tokens will be drained.
Let's test this! Head over to https://learnweb3.io/ and click on the "Connect wallet" button. A metamask pop-up should appear, approve the connection request to sign in and get started! You can try connecting to other dApps since you are using a test account. However, you should still ensure they are secure and trusted. Alchemy has a list of secure dApps to check out here.
Conclusion
We've delved into the world of blockchains, learning how they have transformed digital transactions while still managing to secure data. Blockchains are like supercharged digital ledgers that are reshaping how we interact online. The potential is enormous, from cryptocurrencies to new and innovative applications. Whether you're a newcomer or a seasoned developer exploring this technology, good luck in your journey and happy hacking!
Additional Reading
Ethereum Yellow Paper: https://ethereum.github.io/yellowpaper/paper.pdf
Blockchain scaling Solutions: https://ethereum.org/en/developers/docs/scaling/
Security practices on the blockchain: https://sumsub.com/blog/how-to-ensure-security-when-using-blockchain/
Metamask security practices: https://hashnode.com/post/clifantt2000009ld5ym55cfq